Authentication
The image shows the journey from the end user to the MSL Edge API.
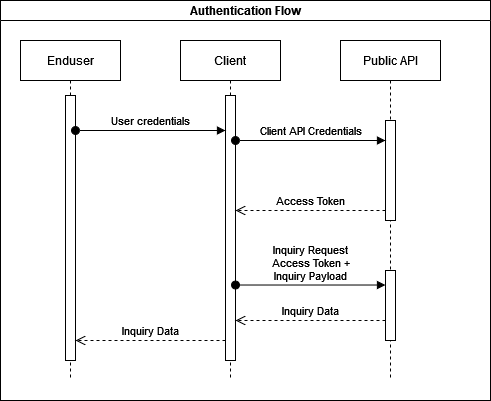
MSL Edge is to whitelist the client partner public IP address/range to allow access to the platform.
Client Credentials
Use the provided username and password for the token request as documented here. If the criteria for a valid username, password and IP address are satisfied the API returns a token.
Authorization Header
Once the API returns a token, the next step is to use it for subsequent API requests. The example shows the Authorization header and the value that must be provided to have an API authorization on an endpoint.
On receiving the token, the platform initiate the validation. It is to ensure requests are from allowed IP addresses and the token is valid.
Password Expiry
After successful authentication, the API returns an access token. The token payload includes the password_expire_days field, which indicates the number of days remaining before the password expires. This value should be monitored so the password can be updated proactively before expiry using the POST /manage/password to avoid authentication failures..
When changing a password, the new password is validated against previously used passwords. If the new password matches a previously used one, the request is rejected with error code 4010001.
Once the password has expired:
- Any attempt to obtain a new access token using the expired credentials will be rejected with HTTP Status Code 401 and error_code 4010001.
- Authentication will not succeed until the password has been updated successfully.
IP Whitelising
When a request to generate a new token is received, the IP from where the request originated is also recorded and used in the token generation. When credentials for making requests to the APIs are being created, a number of IPs or IPv4 ranges are to be provided in order for generation of tokens to be successful. When a request is received, the IP of the request is checked against the IPs or IPv4 ranges provided, and if there is a match, a token is generated accordingly.
Suspicious IPs
Although an IP is whitelisted to authenticate and retrieve tokens, it doesn't mean that its also whitelisted from the Suspicious IPs security feature enabled. If a burst of 20 or more requests to retrieve a token are made in a very short period of time, the IP will immediately be flagged and blocked for a period of approximately 15 minutes. If during these 15 minutes more tokens will be requested, error code 4010001 will be returned to not disclose the status of the credentials provided.